Updated April 25, 2021 – Our team made updates to our interpretation of the phone activity logs to ensure alignment with case reports.
This is an in-depth analysis of data that was found on the mobile phones of Kris Kremers and Lisanne Froon, the two young women that disappeared in Panama in 2014. Kris Kremers carried an iPhone 4 with her and Lisanne Froon carried a Samsung Galaxy S3. After they disappeared, both phones were found in their backpack on the bank of a river. The data that was extracted by investigators tells a story that may offer insights into what happened after the girls had disappeared.
This excellent analysis was done by Matt, whom can be reached at researchtt2@gmail.com. Matt also previously published a thorough analysis of the Night Photos (link) and organized a comprehensive timeline of the Daytime Photos (link). Matt is tremendously strong with data analysis and graphing information. As you’ll see below, Matt’s charts and graphs make it easy to visualize the phone activity of Kris Kremers and Lisanne Froon after their disappearance.
Romain has also published a similar article in French available on CamilleG.
Kris Kremers & Lisanne Froon Phone Data Analysis
This article reviews the phone logs of the iPhone4 and Galaxy S3 mini between 01 April 2014 and 11 April 2014. The data is based on forensic analysis from the Dutch police and other official reports, that were made available to me for review by a source to supports my goals (published on reddit).
This article offers data but no conclusions and no theories.
I would like to stress that the data in this article is not simply data, but it reflects a desperate situation and tragic events in the lives of two young women. This should be remembered and respected.
As with all data, the first question that should be asked is if it is correct and complete. There is no doubt that the phones were the actual phones of Kris and Lisanne, which was confirmed by their IMEI numbers, and content found on them. There is also no doubt that the Dutch forensic examination was truthful and correct, which however does not exclude mistakes or omissions being made.
It is unknown though who was in control of those phones between 01 April 2014 and 11 April 2014. Most likely it was Kris and Lisanne, but it cannot be ruled out with that there were 3 rd parties involved to some degree. It is also not known where the phones were between 02 April and 11 June when the phones were found and who may have been in control of them. Between 12 June and 23 June, the phones were in the custody of the Panamanian police and from 23 June on they were in the custody of the Dutch police.
There was ample opportunity to access the phones and make modifications to the data within. It is unknown if this happened. There is no indication in the forensic analysis that there are signs of manipulation, however it was not specifically looked for.
There are generally two types of data that can and have to be manipulated:
- User generated data like photos and videos
This data is easily deleted by anybody with access to the phone. The iPhone4 had a login code that has to be entered to access the phone. Although it is not clearly stated, it can be inferred that this code was still active and required when the phone came into the custody of the Dutch police. Anybody who would have deleted user generated data from the phone would have needed this code and could have only gotten it from Kris or Lisanne in the period of 01 April to 11 April. The login pin was 0556 and although not very secure, it was secure enough to not be guessed easily. Note that there is no operating system log for when the known pictures were taken, so it is not impossible that other pictures were taken and deleted.
There is however no mention in the police report if any user data was deleted.
- System generated log files
The operating system of the phones (iOS and Android) creates log files for most activities the OS performs. For example, iOS will leave the following entry n the log file powerlog.gz:
03/31/14 20:15:08 [Log] state=booting; existinglogdate=<unknown>; periodStart=<unknown>; rolloverDate=<unknown>; rotatePowerlog Key= Default; logging Mode=Lite; binary=aggregated; pid=38;
Although it is possible to manipulate those entries, it is difficult and requires root access to the phone. This is above the abilities of the average person and requires someone with advanced skills and tools. There is no mention in the forensic report that data may have been deleted or modified, however it was also not particularly looked for.
It can be summarized that it is possible to delete user data when knowing the login PIN to the phones, but it is very difficult to manipulate OS system information. The forensic analysis of the phones themselves is assumed correct.
Fingerprints and DNA samples were taken from the phones. There was no DNA profile recovered and the recovered fingerprints were not suitable for identification. Any results would be questionable anyways since the phones were handled by several people after being found.
The following section will describe the activities found on the phones.
General Analysis
There is no GPS data available for either phone for the time period past 01 April. None of the 911 calls connected to the cell network in Panama. For a call to connect it must ring at least once, but none of the calls did for a lack of cell network connection. For that it is assumed that also none of the 112 calls connected, however the author has no records from the Dutch phone system to show this or otherwise. It is also likely that if “112” is dialed in Panama it would be routed to the 911 center in Panama and not to the Dutch emergency center.
It should be noted that on “the internet” it is often discussed that there were over 70 attempts to enter the SIM pin in the iPhone4. Although, this is correct it covers the time period of March to April and is completely irrelevant for anything that occurred after 31 March.
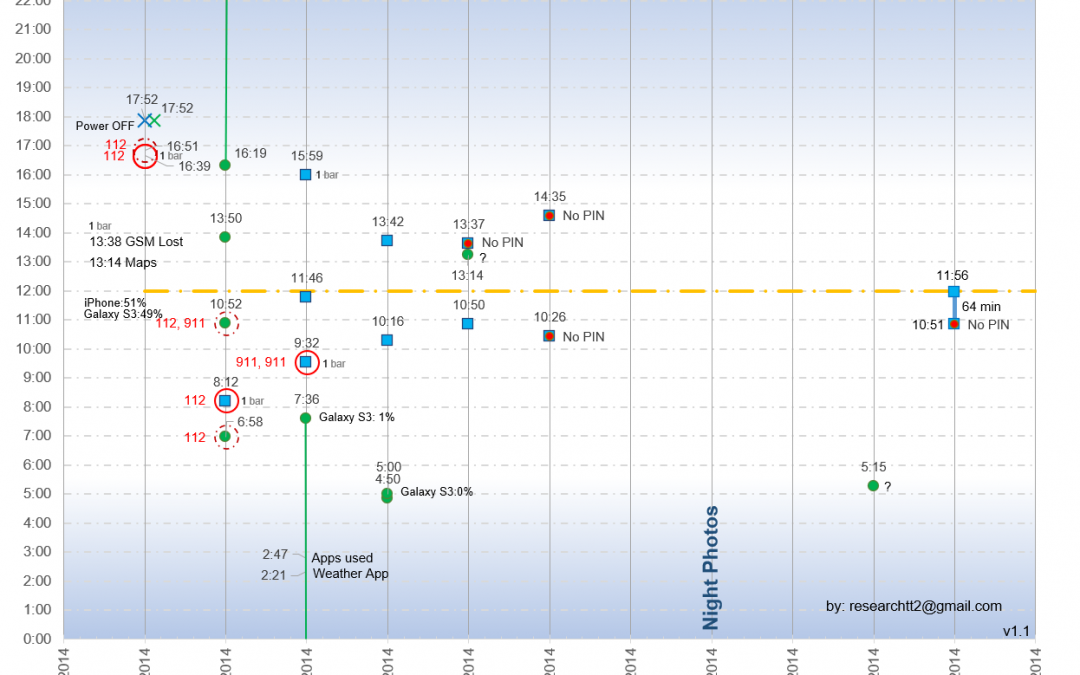
Image 1 below summarized all relevant events. Events are only plotted by day on the x axis but not by time. This means that all activities of each day are on the same vertical axis, while technically the activities later in the day should be displayed further to the right on the x axis. This is done to increase visibility.
For all times where a phone was booted up or shut down, it is represented by a single dot. For all occurrences shown by a dot the phones were turned on for 1-3 min only. Where the phones were turned on longer, it is represented by a line, for example on 02/03 April and 11 April. There is no line representing the time the phones were Powered up on 01 April 2014 as it would be too convoluted and only the times the phones were turned off is displayed.
For this article, all times are given in 24h military time. So 15:00 is 3:00PM and 5:00 is 5:00AM. All times are local time in Panama.
Note that there are some inconsistencies in the forensics report that lead to the activation on 06 April to be interpreted as 13:37 instead of 14:35. This was pointed out to me and is corrected in this article as of 25 April 2021.
The graph now also shows all signal bars for the iPhone4 that are 1 bar. All readings with more than 1 bar on 01 April are omitted to declutter the graph. When there is no indication of signal strength, then because it is not stated in the forensics report and most likely there was no signal at all or 0 bars.
It is not always possible with absolute certainty to determine when a phone was on and in use or only on and at what exact time it was turned off. The data presented here is the best judgment of the forensics expert.
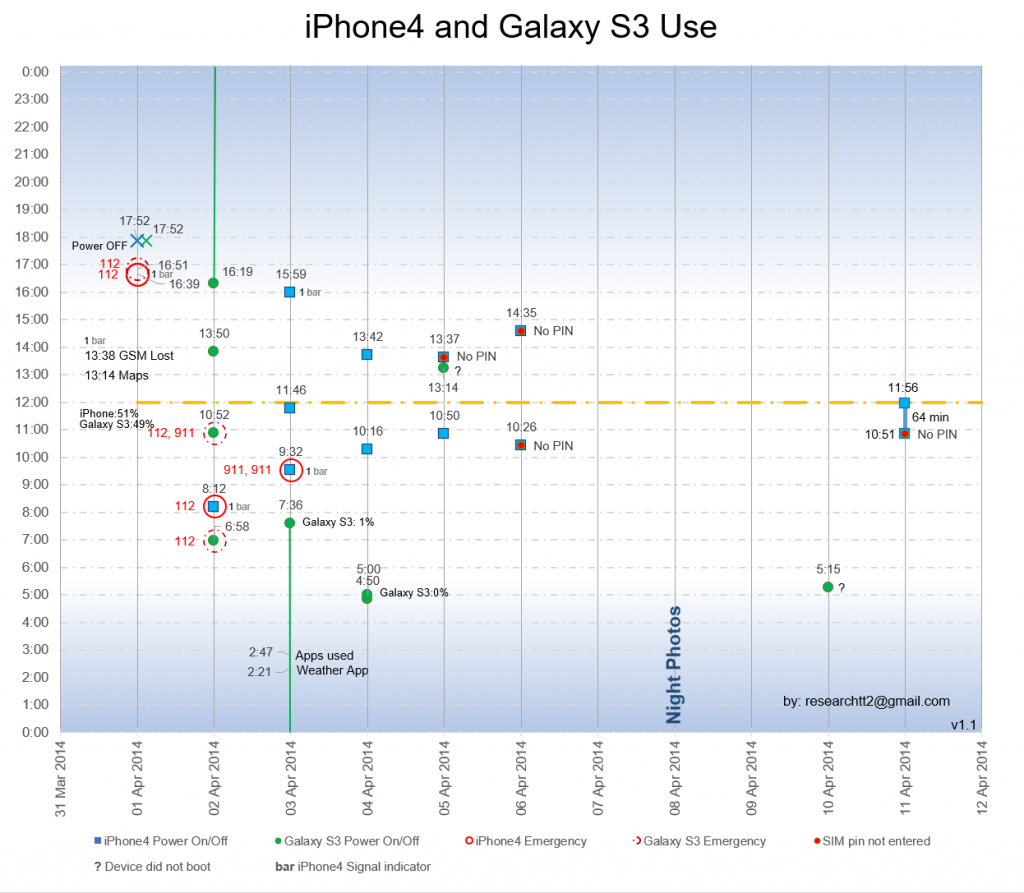
Image 1: Summary of Phone use
The table below shows the signal strength as recorded by the iPhone4 and the bars on the signal display indicator of the iPhone4. The indicator ranges from 1 – 5 bars and those are not just proportional to the signal strength but also are affected by other attributes like connection type (e.g. 2G/3G) etc. If the phone shows 1 bar as it still did on and after 13:38 on 01 April, it does not mean that the phone had a network connection.
The signal strength in dBm is the cell signal strength received by the phone’s transceiver. In order to have a network connection and being able to make phone calls or send text messages, the phone has to establish a two way connection to a cell tower. Since cell towers have large elevated antennas and great signal strength, it is often possible to pick up the cell tower signal but the phone with its tiny antenna and limited transmitter power can not send a signal back. This results in situations where there is a bar indicated on the phone but the phone can not connect to the network and can not make calls.
Signal strength data is shown in the forensics report up until the data point at 15:59 on 04 April. After that, no more signal readings are shown and it is the assumption by the author that from then on, the phone did not receive any signal anymore and did not log signal strength data and it was not listed by the forensics examiner that no signal was detected.
A signal strength of -113 dBm per the forensics examiner means that there is essentially no signal. However it is the interpretation of the author, that the phone transceiver did pick up an extremely low signal.
No signal data is available for the Samsung Galaxy phone.
| Date | Local Time | Network | Signal [dBm] | Bars [1 – 5] |
|---|---|---|---|---|
| 1-Apr-2014 | 11:05:25 | GSM | -82 | 5 |
| 1-Apr-2014 | 11:20:19 | GSM | -85 | 4 |
| 1-Apr-2014 | 11:49:41 | None | -82 | 1 |
| 1-Apr-2014 | 12:33:55 | GSM | -82 | 1 |
| 1-Apr-2014 | 13:14:29 | GSM | -91 | 3 |
| 1-Apr-2014 | 13:14:53 | GSM | -82 | 4 |
| 1-Apr-2014 | 13:15:08 | GSM | -87 | 3 |
| 1-Apr-2014 | 13:16:03 | GSM | -76 | 5 |
| 1-Apr-2014 | 13:16:20 | GSM | -89 | 4 |
| 1-Apr-2014 | 13:38:31 | None | -94 | 1 |
| 1-Apr-2014 | 16:39:26 | None | -94 | 1 |
| 1-Apr-2014 | 16:40:07 | None | -94 | 1 |
| 2-Apr-2014 | 8:13:54 | None | -113 | 1 |
| 3-Apr-2014 | 9:33:32 | None | -113 | 1 |
| 3-Apr-2014 | 16:00:50 | None | -113 | 1 |
Table: iPhone4 signal strength data. Where there are multiple values over a few minutes only the first is listed. Lower numbers mean weaker signal. So -113 dBm is the weakest signal.
Another important factor is the battery capacity. The following image shows the remaining battery capacity from 01 – 11 April. Note that battery data is not available for all days, especially not for the iPhone4 and for those days the battery capacity is estimated. This is possible since the iPhone4 has seen very consistent usage and the battery consumption per day would be very consistent. All data points that were estimated are marked in red. On this graph, data points are plotted at the actual time on the x axis when they occurred.
Between 02 and 03 April the battery capacity of the iPhone4 increases from 42% to 43%. This likely caused by the battery recovering slightly. The battery was not charged, and it is not something of concern.
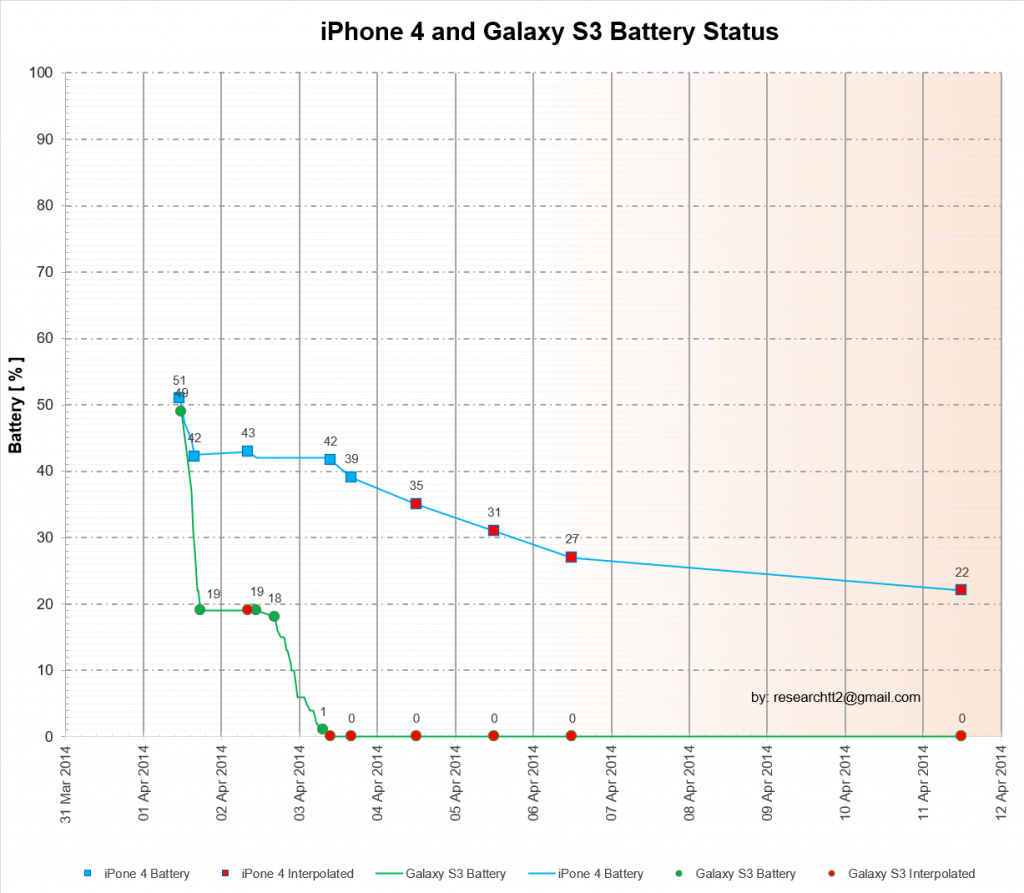
01 April
The last time the Galaxy S3 had a WIFI connection was at 10:10:25. It would never regain another WIFI connection thereafter.
The phones were not fully charged with the iPhone4 having 51% battery capacity at 11:40, while the Galaxy S3 had 49% at 11:40.
Several pictures were taken with the phones between 13:14 and 13:15. Those pictures were most likely taken on the Mirador.
–
13:14
The Galaxy S3 accessed Google Maps.
–
13:38
The iPhone4 lost GSM network contact and would never regain it again. It is likely the Galaxy S3 lost GSM network contact at the same or similar time and it would also never regain network contact. At this time the signal strength was -94 dBm and the phone showed 1 bar. This indicates that the phone picked up a cell tower signal but could not transmit back to establish a two way connection with the cell tower.
–
13:54:58
The last known picture was taken with the Canon Camera, indicating there were no issues at this time.
–
16:39
“112”, the Dutch emergency number was called from the iPhone4
–
16:51
“112” was dialed from the Galaxy S3.
–
17:51:52
The Galaxy S3 was likely powered off. It is not possible to determine this time with absolute certainty. It is concluded based on the fact, that there was no longer any activity of the operating system after this time. It would be logical that both phones were turned off at the same time (the iPhone4 was turned off at 17:52). Note that in the graph this time is rounded to 17:52
–
17:52
The iPhone4 was likely powered off
What happened on this day after 13:54 is not known, however within roughly 2.5h after the last image was taken, something severe enough must have happened to prompt the 112 calls.
It had been nearly exactly 3h since GSM contact was lost and if Kris and Lisanne had been mobile and had the ability to move freely, they could have reversed and moved 3h back towards the mirador and regained contact to the cell network. However, this was not done.
Possibilities for this are:
- They both were not mobile
- They did not want to move
- They both could not move freely
- They did not know the direction back
- One did not want to leave the other potentially immobilized behind
12 min elapsed between the two 112 calls from the phones and 112 was attempted to be called only once with each phone.
What situation is serious but not serious enough to try 112 immediately and instead of trying again, wait 12 min. Even if there was no network contact, why was it not tried more often? Did the phone users have the discipline to simply look at the phone status, see “No Service” and not try again? Is this an indication that, at this time the situation was not yet very serious? Or were they not in control of their actions? Both phones were turned off between 17:40 and 17:52 so at this time it must have been clear that network contact would not be regained and that batteries need to be preserved, which indicates a situation arose that prevented a return to the mirador and indicated a potential wait for help would be required. If they were forced to turn of the phones by a 3rd party, it would be likely the phones would have been turned off at the same time or within the same minute.
02 April
6:58
The Galaxy S3 was powered on, “112” was dialed and the phone powered off. The phone had no cell network connection and the call did not go through.
–
8:12
The iPhone4 was powered on, “112” was dialed from the iPhone4 at 8:14 and the phone powered off. The phone had no cell network connection and the call did not go through. At this time the signal strength was -113 dBm and the phone showed 1 bar. This indicates that the phone picked up a cell tower signal but could not transmit back to establish a two way connection with the cell tower.
–
10:52
The Galaxy S3 was powered on, at 10:53 “112” and “911” was dialed and the phone powered off. The phone had no cell network connection and the calls did not go through.
–
13:50
The Galaxy S3 was powered on and powered off. The phone had no cell network connection, no calls were made.
–
16:19
The Galaxy S3 was powered on and left on. The phone was then powered during the night.
03 April
2:21 – 2:47
The Galaxy S3 had been continuously on since 02 April at 16:19. It appears as if the phone was not actively used and only left on. It is not clear if this was an oversight that depleted the battery or if it was done on purpose.
–
2:21
Weather application used
–
2:41.
Applications of the Android OS were used but it is not known which ones
–
7:36
The battery had depleted to 1% and the phone was most likely turned off at this time or shortly after.
–
9:32
The iPhone4 was powered on, “911” was dialed twice from the iPhone4 at 9:33 and the phone powered off. The phone had no cell network connection and the call did not go through. At this time the signal strength was -113 dBm and the phone showed 1 bar. This indicates that the phone picked up a cell tower signal but could not transmit back to establish a two way connection with the cell tower. A signal strength of -113 dBm per the forensics report means that there is essentially no signal. However it is the interpretation of the author that the phone transceiver did pick up an extremely low signal.
–
11:46
The iPhone4 was powered on and then powered off. For this data point is no raw data in the forensics report and no signal strength is stated. It is possible, that at this time there was also 1 bar but it is not reported in the forensics report.
–
15:59
The iPhone4 was powered on, the contact “Mytiam, 00 507 679xxxxx” looked up in WhatsApp (Note: the spelling in this article is not a typo. Full phone number is withheld) and the phone powered off.
At this time the signal strength was -113 dBm and the phone showed 1 bar. This indicates that the phone picked up a cell tower signal but could not transmit back to establish a two way connection with the cell tower. A signal strength of -113 dBm per the forensics report means that there is essentially no signal. However it is the interpretation of the author that the phone transceiver did pick up an extremely low signal.
This is the last data point for which signal strength data is reported in the forensics report. It is speculation by the author, that from this time on the phone did not pick up any signal anymore and the readings would have been -120 dBm and 0 bars.
No further attempts to call 112 or 911 are made again, which is likely attributed to the fact that the phone had no longer 1 bar and no hope of connecting to a cell tower.
04 April
4:50
The Galaxy S3 was turned on and turned off.
–
5:00
The Galaxy S3 was turned on and turned off. The battery was at 0%. This was the last time the Galaxy S3 booted up.
–
10:16
The iPhone4 was powered on and the phone powered off.
–
13:42
The iPhone4 was powered on and the phone powered off.
05 April
10:50
The iPhone4 was powered on and the phone powered off. This was the last time the SIM Pin was entered correctly. On all previous times the phone was powered up, the SIM pin was entered correctly.
–
13:14
There is a logfile created on the Galaxy S3 which is only possible if the phone had power. However, it did not power up and the conclusion by the author is that the battery had just enough power to start the phone’s boot process, but it shut down from a lack of power before having booted up.
–
13:37
The iPhone4 was powered on and then powered off. Note that at this time the SIM Pin was not entered or not entered correctly (this cannot be determined). The SIM pin will never be entered or entered correctly again. Whoever entered the SIM Pin incorrectly (or did not enter it) must have known the Login pin to unlock the phone.
06 April
10:26
The iPhone4 was powered on and then powered off. The SIM pin was not entered or not entered correctly.
–
14:35
The iPhone4 was powered on and then powered off. The SIM pin was not entered or not entered correctly. Note that this data point was previously incorrectly stated in this article as 13:37 and is also widely incorrectly stated on “the internet”.
07 April
No Activity of either phone could be found
08 April
No Activity of either phone could be found
Note that in the night and early morning the “Nightphotos” (https://imperfectplan.com/2020/11/04/kris-kremers-lisanne-froon-deep-analysis-night-photos/) were taken.
10 April
5:15
There is a logfile created on the Galaxy S3 which is only possible if the phone had power. However, it did not boot up completely and the conclusion by the author is that the battery had just enough power to start the phone’s boot process but it shut down from a lack of power before having fully booted up.
11 April
10:51
The iPhone4 was powered on and left on for 64 minutes. The phone was then powered off. The SIM pin was not entered or not entered correctly.
There are no log files created during those 64 min and it is not known what the phone was used for during this time. The fact that it was turned off indicates that the user had intentions to conserve battery and to use it again. However, it was never turned on again after. It is not known how much capacity was left in the battery but before having been turned on the capacity would have been in the range of 22% and it is likely that some capacity remained when it was turned off. The author believes that there would have been sufficient battery capacity to boot up the iPhone4 again.
Looking at the phone activity data, several observations stand out:
- Emergency calls after the initial ones on 01 April were only made in the morning and only for the first two days
- The Galaxy S3 was generally turned on more often. On 02 April it was turned on 4 times while the iPhone4 was only turned on one time.
- The Galaxy S3 was used during the night and early mornings, while the iPhone4 was never used before 8:14 and on most days not before 10:00 AM.
- The iPhone4 was deliberately used to conserve power, while the Galaxy S3 was used for long periods of time draining the battery quicker.
- There are significant times at which the phones were used most, between 10:00 – 11:00 and between 13:00 – 14:00
- There are distinct differences in the use of the phones
The following questions can be raised:
- Why was the SIM pin not entered correctly after noon on 05 April?
- Why was no phone used between 06 April and 10 April?
- Why was the iPhone4 turned on for 64 min on 11 April?
- Why was the iPhone4 not used again after 11 April?
- Why was no note or message left in the phones?
Image 4 shows at which time of day the phones were most used. The data is accumulated from both phones and between 02 April to 11 April. It shows that 45% of all the times the phones were turned on it was done between 10:00 and 11:00 and 13:00 – 14:00. There must have been cue or indication for this. Was it the sun that came over a mountain at that time? Was this the time to rest from trying to walk to safety? Or was this the time they woke up when they slept during the day since it was not possible to sleep at night? It should be noted that the Canon camera can be used as a clock as it displays the time in the setup menu, so if certain times were targeted deliberately it could be done by using the clock in the Canon camera.
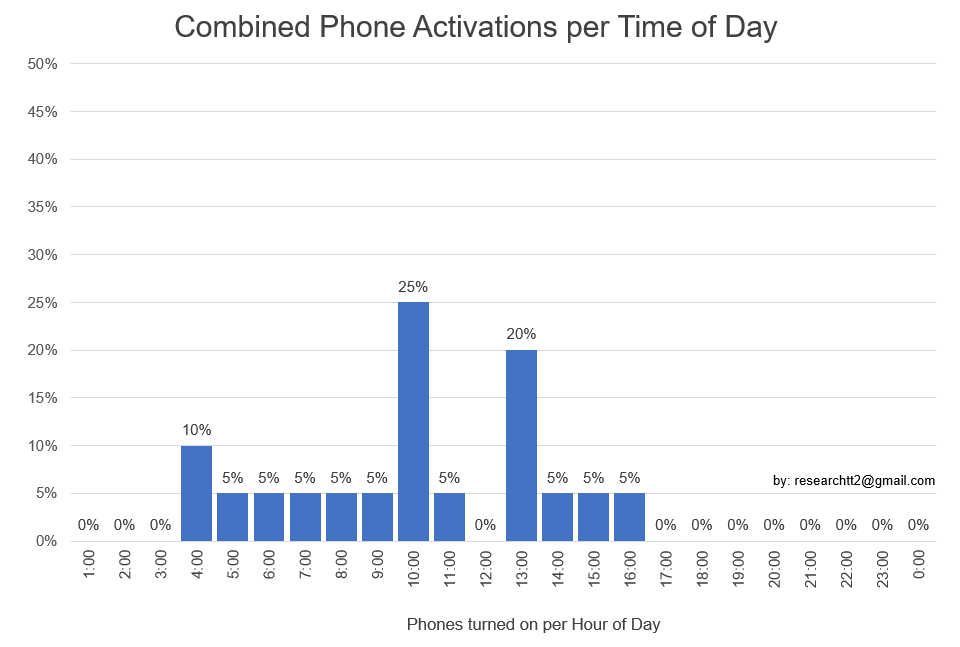
Image 4: Combined phone user per hour of day
Phone Data Summary
There’s a lot to take away from this analysis. Many thanks to Matt for his rigorous and comprehensive work regarding this case. His observations and questions posed above are important to the effort of moving the case forward.
As Matt mentioned early in this article, the purpose of this article was to share data and organize the data in a meaningful way. The purpose of this article was not to draw conclusions, nor speculate on theories.
Our team is focussed on gathering and organizing information about the disappearance case. Our team places less emphasis on theorizing and guessing what could have happened. We know that there is still not enough information about the case to formulate conclusions about what happened to Kris Kremers and Lisanne Froon. Instead of speculating, we’re focussed on gathering more information and analyzing the existing information.
Again, many thanks to Matt for his expert work. You can reach Matt directly by emailing researchtt2@gmail.com
Please note: Our team is committed to accuracy of information and respecting the privacy of those involved with this disappearance case. If you have any supplementary information regarding the case, or if you were involved in this case and feel that the information available in this article impacts your privacy, please contact our team.


I wonder, noone of the search team or their relatives, tried to call any of the two phones, or contact them by any mean? That being sms, telephone call, whatsup call etc?
Hey, Chris and Matt! Thank you for your amazing work on this case!
I wonder if it is possible to make some theories about the girls’ location based on the information about the signal strength and locations of cell towers. I understand that there are a lot of variables, like, one can stay almost in the same spot and have a different reception in a cave and in the open space, for example. But maybe there are some consistent patterns?
Somebody made a comment wondering if they were using a Panamanian sim card. I am actually curious if the did, which company it was. At that time there was Cable and Wireless with is MasMovil, Movistar, and Claro. As is probably true everywhere, these three dont have the same coverage everywhere. I dont know how this would make any difference with the case but I am curious none the less.
The SIM card doesn’t matter when it comes to emergency numbers. You don’t even need sim card to make such connection. You can see this when you have got very poor signal and your phone displays the “Emergency calls only” notification, which means the phone couldn’t estabilish connection with your operator’s BTS, but in can use cell tower of other operator (provided it is in rage) to make emergency call.
Джейк 30 марта 2021 г., 00:14
К тому времени самсунг был мертв, и сим-код айфона для последнего был правильно введен 5-го числа. Для того, чтобы использовать фонарь, вам нужно включить телефон, что означает правильный ввод сим-кода.
_________________
Нет, это не так. У моего айфона 4 (2011-2019) фонарик можно было включить на заблокированном экране.
I’ve been creepily fascinated by this case for years….I just can’t wrap my head around a couple of things:
Why didn’t either one try to text either using the phone or through Whatsapp….when calls won’t go through, sometimes texts can….why didn’t either one at least try? It’s so strange to me – nothing suggests there were texts left in drafts unable to be sent, or any other calls aside from emergency.
The other thing that really bothers me is that they left no other pictures or messages to their families…
Maybe it was suicide? The girls seemed pretty disillusioned with the trip.
Or they simply wanted to get away from the town for at least a few days.
As for phone use, it’s as if each girl kept watch on the other, taking turns between sleeping.
If hurt, it’s possible they didn’t get too far, staying in the same place, particularly after the 6th: hungry dehydrated and weak.
Hi, so I noticed it said they looked up somebody on Whatsapp. I read the trip advisor reviews for the Tour Guide and they are mostly 5-star reviews but they appear to be written by the same person. 3 reviews in a row mention how it’s best to contact him via Whatsapp.
If you read the reviews, they start talking about how he leads tourists down “hidden trails” and they meet “indigenous people”. They also mention how he knows a little “Dutch”.
Is this all coincidence and just me thinking too much about this? Or is that Whatsapp the tour guide? Could someone have tampered with Whatsapp messages?
I just question this because if you’re going to look up someone on Whatsapp, wouldn’t you also look up anyone else? Why one specific person on Whatsapp?
One thing about those no pin / incorrect pin entries troubles me. It is said everywhere that it can’t be said whether pin code is entered incorrectly or it is not entered at all.
However, doesn’t SIM card get locked if the pin code has been entered entered incorrectly three times in a row? After that you have to enter PUK code.
So, shouldn’t it be possible to examine if there is less than 3 tries for pin code to Kremer’s phone? And if there is, the incorrect pin has been entered. If all the three tries are still there, no pin has been entered?
Hi Chris,
your analysis of the phone data is well done.
May I remind you, that a very important info is missing:
KRIS HAD A PHONE CALL ON APRIL 1ST with her friend in Netherlands
at around 2pm local time (in Panama). This information comes from a very early
interview of the Kremers family. The father mentions the call in the interview, thinks it
was 2 pm in the Netherlands. But he is then corrected by his wife and they agree to that
the conversation between Kris and her friend took place at around 2pm Panama time.
It is not stated if either Kris or her friend placed the call!
Why is this important data missing in the data of april 1st?
Has it not been in the phone? If yes, why not?
If that call at 2pm took place, they must have had reception and this would contradict your entry of april 1st, 13;38: IPhone of Kris lost signal and never regaind it again.
Can you clear this?
Best regards, Thomas
Hi Thomas, thank you for your comment.
Yes, this is the subject we’ve come across before. The challenge is that there’s no evidence in the official police records that indicate that a call was made on April 1st. Although the parents claim that the call happened on April 1st, we simply don’t have any proof of the call. So, it’s difficult to make a determination on how this should be evaluated and we must be cautious about presenting this as fact.
The only information we’ve identified that could be related is that Kris’s iPhone was used on March 31st around 2:00PM, for WhatsApp and general internet browsing. Still, we’ve found no official information that claims a call was made around 2:00 on April 1st.
Thank you again for your comment. Cheers!
A phone is often used as a light in the dark. So I wouldn’t be surprised if they let the Galaxy on that night to have a light source or to use the flashlight.
Very interesting read, and keep up with the research!
Plain and simple, the phones were not in their possession starting from 17:52 on Apr 1st.
These phones have compass apps, that don’t need network connection. GPS that doesn’t need network connection. The map apps do need network connection to show the map, but if they used it before in Boquete, the map tiles would be cached. Even if the map shown is blank, it will still help with orientation North/South etc.
Did they use local Panama SIM cards?
Either way, you try to call the emergency number when there is an emergency. If you are just lost, first you try the map app. But if the emergency number didn’t work, try to text your parents, or your host family, or the Dutch boys they met earlier on the coast.
They did none of this. And by the way, they are on a well frequented tourist trail from where it takes at most 2 hours to walk back down to Boquete. All they need to do is take the trail back.
I guess it is possible to use the camera as a clock, but wasn‘t the time wrong and had to be adjusted? I experimented with a viewscreen as a flashlight and it does a fair job in pitch darkness. Wonder if it is able to be determined when the camera was powered on and for how long. That would be amazing data
Also could be interesting to know the camera settings, if the lcd brightness was set high, if the display was set to show clock.
Interesting to see the data on charts. I had always thought there were 70+ attempts to use the phone after the 6th. I think even travel channel program said that. But here you are saying that was for march and april? I noticed they did not wear wristwatches, and i know if i was in that situation i would be using the phone to check the time. Yet somehow whoever used the phone seemed to power it up close to the same time twice for a few days even after the wrong code was entered. I thought before reading this blog that there were dozens of possibly panicked desperate attempts to use the phone. Seeing the chart really changes things.
I have a few things that I question about this story. I want to say that I live right on the edge of having cell signal at the base of the Appalachian mountains. Without Wi-Fi calling I would miss most calls and text when I am at home. At the end of my driveway I get 2 bars and no matter which way I turn my signal just gets stronger. If I go out on the front porch during the day I can most of the time get enough signal to make calls yet once it gets dark and later at night I can make and receive calls almost anywhere in house. At night I get more signal than day. https://forums.macrumors.com/threads/better-signal-at-night.1084008/ that leads up to my 1st issue. Why did they not try to make calls at all after 5 pm in afternoon? 2nd issue is if as really might have happened that 1 or both was hurt and Kris became unconscious and could not put her pin in her iPhone would Lianne not have asked her what her pin was before she became unconscious. That speculating that she did not already know it. I know my best friends pin to his phone. Just over the course of hanging out I have had to make a call from his phone (to find mine). Yet no matter if she knew or not anyone would have asked her for the pin if she was hurt. Like hey let me do that for you at the very least.
Guessing about any thing else is guessing. Just like my questions are just wondering why these things happened. These are all things we may never get an answer too.
I am reading into the whole case again and I just noticed that it might not have been discussed before or i mightve missed it.
I dont want to suspect anyone but what I find very unusual is that the PIN was last entered correctly at the same time, as the young guy Osman went missing (http://elsiglo.com.pa/cronica-roja/chiricano-perdio-vida/23448763) and was never correctly entered after he was discovered dead.
To be precise on April 5, 10:50 am the PIN was entered correctly for the last time. Osman was reported missing on April 4, 6pm and found dead on April 5, 1pm. So this is a very huge coincidence?!
Of course the found swimming photo is highly speculative but the circumstances are very suspicious.
This puzzles me greatly:
“15:59 – The iPhone4 was powered on, the contact “Mytiam, 00 507 679xxxxx” looked up in WhatsApp (Note: the spelling in this article is not a typo. Full phone number is withheld) and the phone powered off.”
This is done on 3rd of April. 00507 is country code of Panama. Wasn’t Myriam owner of hotel they were staying in? Is there any other reason they might have looked her up other than to call for help?
Yes, I think they wanted to call the mother of their guest family for help.
But obviously, from the entry in the search field of whatsapp, they didn´t have Myriam´s phone number with them! Why else would they enter the phone number there?
The intreresting thing – they tried to contact her only on April 3rd. And if I understand correctly they did have the number (because it is cited), but did not call her.
If the number was looked up and not dialed, i thought 2 things: perhaps you look up a number to give to someone else to go access a phone, someone promising to call to let myriam know where you are. Or her name came up in conversation with another party regarding where they were staying, and 3rd party looked at the phone to see if they could find where myriams place was located.
Well done to Matt for putting the info together. There is a simple explanation regarding erratic phone use towards later stages. In some general responses, there has been an attempt to paint the girls as “smart and sassy“ Politely this is ludicrous. The girls crossed the Continental divide without a map, without knowing where they were going and its danger, with inadequate clothing, little or no food and perhaps just a couple of small bottles of water at the most. Definitely not smart and sassy. I ride motorcycles in remote mountain off road tracks. Even with a map and a days planning it is easy to get lost. I can tell you ,you have to control your emotions strongly because it is very easy to start to panic even well prepared with a lot of experience.
I believe that the girls would be so traumatised particularly if one of them was suffering infection or serious injury, that they would be incapable of thinking straight and doing things in a rational manner. Liz mentions her own fragility in her diaries and her parents allude to that as well. This does not prove what happened to them but for those looking to explain unusual phone use as a hypothesis for something else are on thin ground. The author of the post specifically mentions he is not and I am not aiming at anyone here rather than tons of the stuff I have read about the case. I have always thought the best way is to establish what happened through concrete groups of evidence. It is nice to see somebody having the time and facility to do that . Unfortunately most people just seem to sit down ,read through the basics and then construct an entire theory based off their own feelings. Whilst this is interesting reading it is of little use. Instead of investigating the case like is done here ,lots of time is spent arguing over the various hypotheses. And well done to Scarlett one incredibly bright and smart woman.
I find it at least interesting to note, though I don’t know what it means, that Kris Kremmers didn’t appear to have her iPhone 4 on her person in any of the last photos that were taken near the stream. Although she appears to have a water bottle, no phone is visible in her shallow front or rear pockets of her shorts. I find that somewhat strange, even if the scenario were that Lisanne Froon had possession of the Canon camera and was taking photos, that Kris, a young woman on a hike, would not want her iPhone physically on her person. The reason I write this is because it would seem to me that a young woman who is hiking with a friend would still want to be in the process of taking her own photos on her phone should she choose to. Also, most people hiking would logically want to have a phone in their possession (rather than in their partner’s backpack, let’s say) just in case anything happened and she might need to access a phone quickly. This is pure speculation, but one possibility is that when the photos of Kris by the stream were taken, she had already somehow been separated from her iPhone, if only temporarily. But of course, there could be many explanations.
The girls took turns carrying the backpack. Therefore, I see no problem to put the phone in a backpack, because it is very easy to lose the phone from a small pocket.
The problem with any women’s clothes is the small pockets. Pockets on coats, jeans and trousers are only suitable for something the size of a matchbox. The designers do it so that they can sell more purses and handbags…
But, during a once in a lifetime journey, would you choose to still have your phone in your hand all the time to take pictures and videos?
Next question: I’m 100% sure that family/friends would have send them textmessages and whatsapp messages, on the first days of their disappearance. Also phone calls etc. Didn’t any of them went through?
Hi Fred, I think a reason for that we don´t see the cellphones might be, that K+L had decided to carry the phones inside the backpack. To protect them from being damaged in the tight shorts or in case of slipping or falling. Anyway, the phones stay accessible in the backpack, which they took turns in carrying.
I go on hikes with my husband frequently in and around streams and rivers. Woman’s pants have tiny pockets, and I don’t want my phone falling out of them into the water and getting damaged. I almost always have my husband put my phone in his deeper pockets or whatever bag we have. That’s just my 2 cents though!
My theory about the usage of the phones.
Each were trying and looking for signal only once to save battery. They kept moving and periodically turned on phones to check signal and sometimes make call attempts.
The samaung may have been left on overnight by accident.
Kris probably was not able to put her pin after the 5th, either being unconscious or deceased.
Lisanne, since her phone was dead, tried to use Kris’s phone, didn’t know the pin or didn’t have to use it to unlock it for emergency calls and was just checking for signal.
Not having power on her phone and unable to use Kris’s phone, Lisanne used the camera, for attention or as source of light.
As we see Lisanne possibly tried to power her phone even after the battery was dead in hopes of maybe checking for signal.
Is wierd why no messages were left. Maybe they never stopped hoping or being in a distressed situation they didn’t think of it.
I think Kris was deceased of possible serious trauma, for example bleeding by accident and was deceased on 5th, hence no pin was entered afterwards on her phone.
Lisanne kept trying in hopes of locating signal with Kris’s phone or calling for attention with camera but unfortunately was deceased because of hunger/dehydration on 11th, hence no more attempts even with enough power on Kris’s phone.
The girls may have located, from what it looks like a river or ravine and have been following it in hopes of getting back, but in the wrong direction. The coordinates of their bag spotted, when looked on Google earth, I would follow to the North, which is wrong instead of south to get to nearest town.
The phones were found on June 13 and handed over to the police on June 14. Why do you write that the phones were found on June 11? this is so unprofessional, can we trust your information and reasoning?
Hi Vlad,
The official police report stated that the phones were found on June 11th.
It’s understandable if you don’t trust the official police reports. However, please provide evidence to support your alternative claims. Where did you learn that the phones were found on June 13th?
If you do not provide solid evidence of your claim, I will need to remove your comment. As you can imagine, our team is are very cautious about the spread of rumors and unverified information.
Cheers
Hi Chris, thank you for your answer.
As far as I know you are familiar with blog CamilleG, below I attach a link to her post, where she writes that the backpack was found on June 13, 2014.
https://camilleg.fr/le-projet-el-pianista-sur-les-traces-des-disparues-du-panama-2/
I think CamilleG made a mistake because I found confirmation that the backpack was found on June 11, I was wrong!
https://www.prensa.com/redaccion_de_prensa-com/Indigenas-encuentran-holandesas-Bocas-Toro_0_3958104151.html
I have another question, why is the photo of Chris’ shorts black and white? is there a color photo of the shorts?
I mean Kris shorts
Hi, after following that case for a time and reading and watching all what is available on the internet, I believe it was foul play involved at the beginning. Like the girls were followed and taken and later managed to escape and fell down a ravine and got injured. What I always found very suspicious is the death of 3, or was it even 4 young guys, who had contact with the girls very soon after they got missing. That stinks! My daughter was travelling through Panama when she was the same age as Kris & lisanne and had a few issues with the local boys as they were very pushy and some under influence of drugs as well. Columbia not far away…
Most or all of the clock times weren’t random, but they were intentionally chosen. Very interesting clock times! If you haven’t done it yet, learn what various numbers mean.
Do you a have a theory?
It’s very strange that the phone wasn’t turned on at all on the night of the 8th, when the night photos were taken.
You would think that if they were active that they’d be using it as a torch, or a signal light, unless they were using the camera screen for light.
So much about the phone and camera usage just doesn’t make sense.
By that time the Samsung was dead and the iPhones sim code for the last was correctctly entered was on the 5th. In order to use the torch you need to have the phone powered up, means having the sim code put correctly.